HTTP Full Form – Hypertext Transfer Protocol (HTTP), HTTP Definition, HTTP Methods, Idempotent, Non-Idempotent, And Safe, Unsafe Methods
The full form of the HTTP is Hypertext Transfer Protocol. HTTP (Hypertext Transfer Protocol) is the most popular and widely used web-based Application layer protocol based on the conceptual model of the Internet protocol suite. In the OSI model HTTP protocol, it belongs to Layer 7 called the Application layer.
HyperText Transfer Protocol (HTTP full form) transfers and combined the hypermedia information in World Wide Web (WWW). HTTP is the Standard protocol for Web Browsers that helps users exchange hypermedia information from one place to another through the Internet or World Wide Web (WWW).
The Hypertext Transfer Protocol (HTTP full form) helps to communicate hypermedia information between clients and servers.
HTTP Protocol Works based on Request-Response protocol between Clients and Servers, The Client may be a web browser or User-Agent, and the server may be a Web server or any other host, etc.
HTTP was initiated at CERN in 1989 by Tim Berners-Lee and also the inventor of the World wide web (WWW) HTTP/1.1 first documented in RFC 2068 in 1997.
HTTP Working Group was formed in 2007 and refined the HTTP/1.1 Specifications. In the year of 2014 June month, The Working Group (WG) Release six updated specifications.
- Message Syntax and Routing – HTTP/1.1 (RFC 7230)
- Semantics and Content- HTTP/1.1 (RFC 7231)
- Conditional Requests- HTTP/1.1 (RFC 7232)
- Range Requests- HTTP/1.1 (RFC 7233)
- Caching- HTTP/1.1 (RFC 7234)
- Authentication- HTTP/1.1 (RFC 7235)
- HTTP/2 was published as RFC 7540 in May 2015.
Table of Contents
1. HTTP Version released Year
- 1991 version 0.9
- 1996 version 1.0
- 1997 version 1.1
- 2015 version 2.0
- 2018 version 3.0
2. HTTP (HTTP Full Form is Hypertext Transfer Protocol) Request-Response Architecture (purpose of HTTP protocol or use of HTTP protocol:
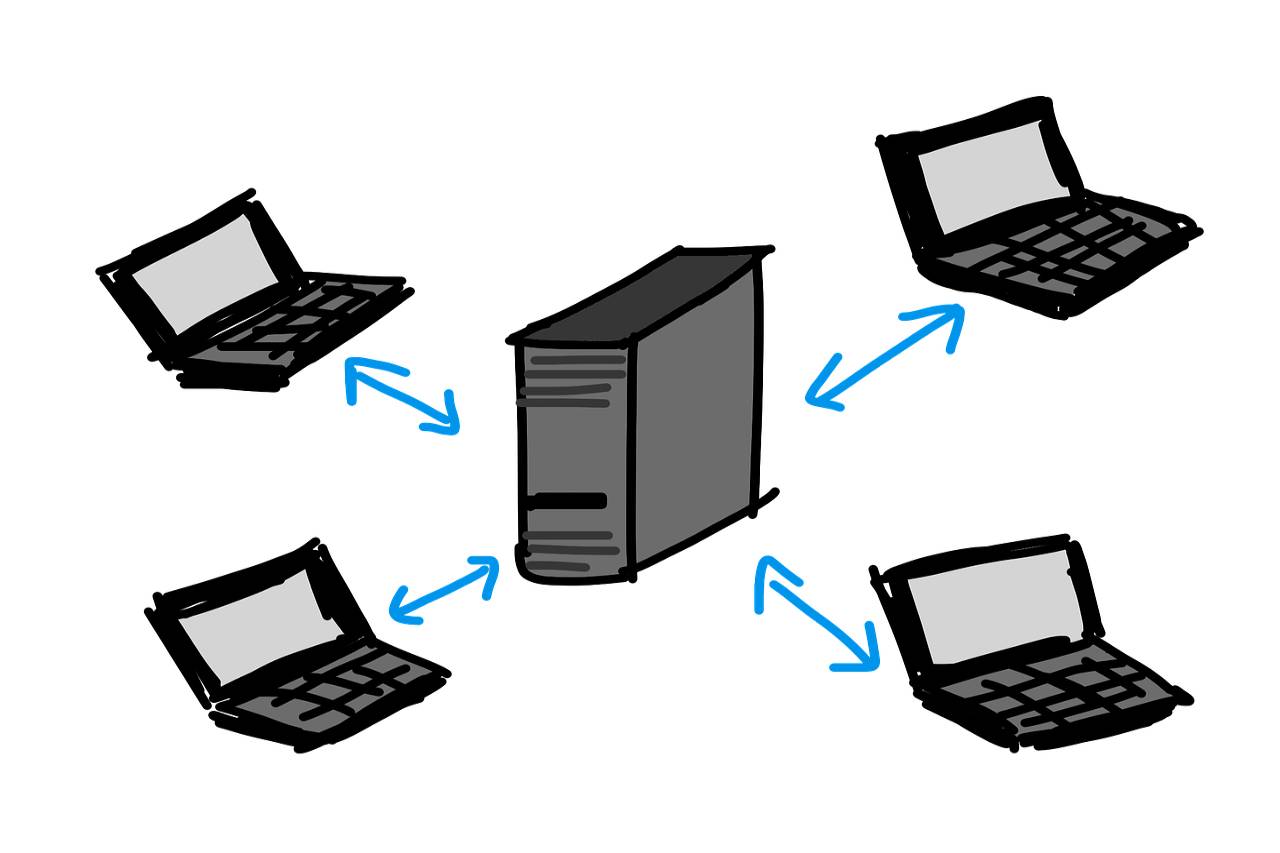
If the user requests the query from the Client (Browser), The HTTP Protocol takes the information and sends it to the server (webserver), If the information is available on the server, the server responds as per the user’s request or if the information is not available in the server, the server returns the information source as not found in the server as per the user’s request.
HTTP protocol Is the media between the client and the server for exchange or transfers the hypertext or hypermedia like any Text, Audio, video, any other data files, etc.
3. HTTP Methods or HTTP Verbs:
HTTP Defines Some Methods Sometimes we referred to HTTP Verbs
All HTTP Methods Names are Case Sensitive is
- GET
- POST
- HEAD
- PUT
- DELETE
- OPTIONS
- PATCH
- TRACE
- CONNECT
4. HTTP GET Method:
HTTP GET Method is the most generally used HTTP method for requesting data from a specific source; it means it retrieves the data from the web server using parameters in the URL place.
The HTTP GET method can transfer a limited amount of data from the client to the server because data will send in the header.
The request parameter would be a string. The query string written in the URL is a key-value pair. The GET Method is used for requesting data from a specific source.
GET is a method to send a limited amount of data because data can be sent or transferred in the header by passing URL parameters called query strings (key-value pairs).
The GET request method is not secure because data is visible in the URL, and users can bookmark the requested data in the browser.
GET Method requested data is idempotent or called a safe Method, which means the second request is rejected or fails until the response of the first request is delivered.
The GET method is adequate and used more than other HTTP methods like a post.
5. HTTP POST Method:
In the HTTP POST method, the request data will be a significant amount, because data send in the message body. POST Method is used to create a new resource on the server.
The POST method is secure because the POST method request will not be visible in the header, i.e., the URL’s Query String.
You can’t bookmark the HTTP POST request.
The HTTP POST method request will be non-idempotent. For example, If You called or Send the same POST Request Multiple times or N number of times, You will get Multiple new resources on the server. It sends the data to the server (secure data compare to the GET Method) for creating or Updating the data.
The POST method request is adequate and used less than the Get method.
6. HTTP HEAD Method:
HTTP HEAD method is nearly similar to the GET Method but without the response body.
HTTP HEAD Method is used to get Response status only and also receives the header’s information from the web server with nobody (Records).
HTTP HEAD Method is used to find whether the source exists in the server or not by the Analysis of Response status or Response Header information, for example for Testing, whether the hyperlinks are valid are not.
The Response Meta Data or Information in The HTTP Header of the HEAD method is identical to the Response Meta Data in The HTTP Header of the GET Method. The difference is that the response of the HEAD Method Request doesn’t contain the message body.

7. HTTP PUT Method:
HTTP PUT Method is used for Sending the data to the webserver to Create a new record or update an existing record.
The Difference between the HTTP PUT and POST Methods is That the PUT Method is idempotent, and the Post Method is non-idempotent. For example, If You are requesting the same HTTP PUT method multiple times on the server, The HTTP PUT method produces the same results. Data will not change; it just overwrites the same data because it is idempotent.
If the HTTP Methods don’t modify or change the resource or data in the server Those methods are called safe methods, PUT and POST methods are unsafe methods because data can be modified in the server.
8. HTTP DELETE Method:
The HTTP DELETE Method is used to Delete the resource or data in the server.
If You request or call the same DELETE Method request Multiple times, The first Request of the DELETE Method Deletes the data or information and the response will be 200 (OK) or 204 (No Content), Remaining request response will be 404 (Not Found), the remaining request responses are different from the first request, there is no change of data in the server because original data already deleted, so DELETE HTTP Method is Idempotent.
9. HTTP OPTIONS Method:
HTTP OPTIONS Method specifies the communication options for the target resource (server).
It Means The HTTP OPTIONS Method is used to find out HTTP Methods and the web server will support the remaining Options.
10. HTTP PATCH Method:
HTTP PATCH Method can modify the data, It Means the HTTP PATCH Method request changes the Resource information (Not the complete Information resource).
11. HTTP TRACE Method:
HTTP TRACE Method was designed and used for diagnostic purposes. The HTTP OPTIONS and TRACE Methods should NOT have side effects.
HTTP TRACE Method used For debugging, developers can see what changes have been made after debugging.
12. HTTP CONNECT Method:
The HTTP CONNECT Method Creates a Point-to-point Communication Between Two Devices, HTTP CONNECT Method can be used to create a tunnel to the Secure Device or Machine.
HTTP tunnel or HTTP Tunneling Creates a Data or communication Network between two Devices.
The most General form of HTTP tunneling is the standardized HTTP CONNECT method.
HTTP CONNECT method is used to access Websites That use Secure Sockets Layer (SSL) or HyperText Transfer Protocol Secure (HTTPS). The secure connection is established by using the HTTP CONNECT Method.
13. HTTP Safe and Unsafe Methods:
GET, HEAD, OPTIONS, and TRACE methods are Safe HTTP Methods, Remaining HTTP Methods like POST, PUT, DELETE, CONNECT, and PATCH.
14. HTTP Idempotent and Non-Idempotent Methods:
POST, CONNECT, and PATCH these three HTTP Methods are Non-Idempotent Methods, Remaining HTTP Methods like GET, HEAD, OPTIONS, TRACE, PUT, and DELETE are Idempotent Methods.
Helpful Resources:
1. What is Google Chrome Helper, How Can It Help You?. Why Does It Use so Much RAM?
2. How Secure is a VPN? and Why Do You Need A Secure VPN?
3. What are Robotic Process Automation (RPA), Tools, Layer Design, and its Applications
4. Deep Learning (DL) and its Applications
5. 10 Best Programming Languages For Artificial Intelligence (AI)
6. Artificial Intelligence (AI) or Machine Intelligence (MI)
7. Machine learning (ML) Algorithms and their Applications
Tech India Today
Related posts
Recent Posts
- How Important is Competitor Analysis? November 13, 2023
- Securing the Internet of Things: A Growing Concern October 2, 2023
- When DevSecOps Shines: Reinventing Software Development May 17, 2023
- Implementing Infrastructure As Code (IaC) With DevOps April 21, 2023
- What Can You Gain By Choosing a Reputable HVAC Software Solution? March 19, 2023
Categories
- Artificial Intelligence (AI) (18)
- Augmented Reality (AR) (5)
- Automotive (7)
- Blockchain (2)
- Business (45)
- Career (4)
- Cloud Computing (6)
- Computers (4)
- Content Management System (1)
- Cryptocurrency (1)
- Cybersecurity (7)
- Data Science (1)
- Digital Marketing (32)
- E-commerce (1)
- Education (6)
- Electronics & Hardware (10)
- Entertainment (5)
- Finance (9)
- Gadgets (23)
- Games (3)
- HTTP (3)
- Industry (2)
- Infographics (3)
- Internet (138)
- Internet of Things (IoT) (22)
- Job (3)
- Lifestyle (2)
- Machine Learning (7)
- Marketing (45)
- Marketplace (2)
- Mobile Apps (20)
- Natural Language Processing (2)
- Network (15)
- News & Trends (15)
- Operating System (OS) (6)
- Programming (10)
- Robotic Process Automation (RPA) (13)
- Security (19)
- SEO (24)
- Social Media (29)
- Software (35)
- Tech India Today (1)
- Technology (166)
- Virtual Reality (VR) (2)
- Web Apps (12)
- WordPress (1)
- Workflow (2)
- Workforce (2)
- Workplace (1)
- Workspace (1)